Introduction
Since it's launch 6 months ago, @plentyofphish intercepted hundreds of phished and hacker accounts.

What Do We Do?
- We keep track of all the hacked accounts. This includes those spawned by hackers, permanently under hacker control, and awaiting recovery.
- The 'mute' list of @plentyofphish doubles as an on-chain repository for on-demand use by other services.
- The @plentyofphish keyholders provide guidance to phishing and hacking victims in order to help them restore ownership of their Steem accounts.
Scope
A. Phishing/phished accounts B. Hacking/hacked accounts C. Suspicious transactions indicating A or B
@plentyofphish is a flag/upvote account: it flags phished and hacked accounts but can also upvote victims to help them restore a bit of reputation. It's upvotes are reserved for cases of need and are given as resources allow.
Readme Document for more information.

Keyholders
The following individuals have the posting keys to @plentyofphish. Four of them are from the @steemcleaners team and two are independent abuse hunters.
@bullionstackers (lead user) @guiltyparties (+ master password) @pjau @logic @arcange @patrice
Repositories
https://github.com/gryter/plentyofphish
The @plentyofphish repository ensures there is a centralized point of contact. It will also give support for all individuals who fall victim to phishing.

New Website
The @plentyofphish repository and project now has a brand new website:
https://www.pofpofpof.com
Why 'pofpofpof'? It's actually 'pofp pofp pof(p cut off)' to play on the repetitive nature of phishing. It's also easy to remember.

How Widespread is Phishing?
- a total of 890 accounts have been processed.
- @plentyofphish has 734 accounts on its phishing list.
- 666 accounts are currently under hacker control, most of them are no longer recoverable.
- 155 accounts were recovered.
- 68 accounts were spawned (created) by hackers to phish with.
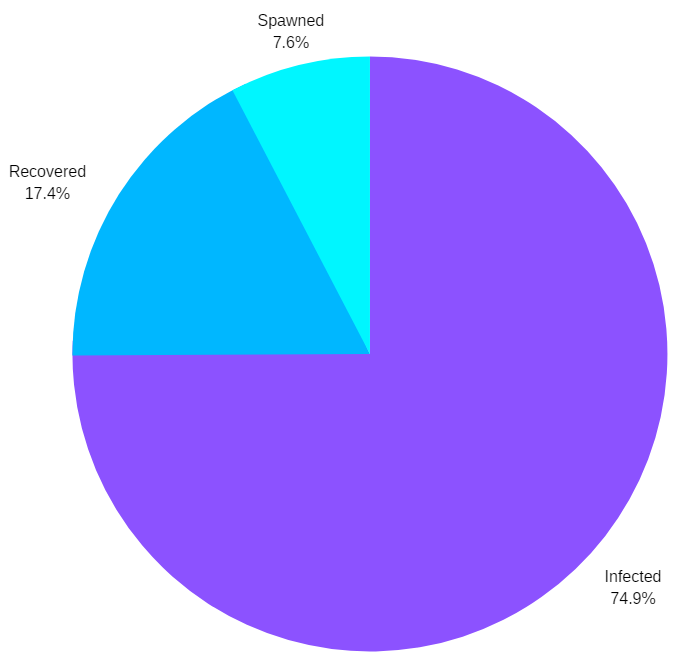
As you can see, the majority of the accounts that are compromised are never recovered. Most are abandoned by the victims who lost everything.
List of Accounts Under Hacker Control
The official list of accounts that are either infected, spawned or irreversibly controlled. It is stored online (on-chain and off-chain) and offline. 1. @plentyofphish's "mute" list (account is muted) 2. GitHub repository list 3. Steemcleaners API http://list-api.com 4. Offline Excel spreadsheet 5. Google Docs Excel spreadsheet
Manipulation of the list is impossible.
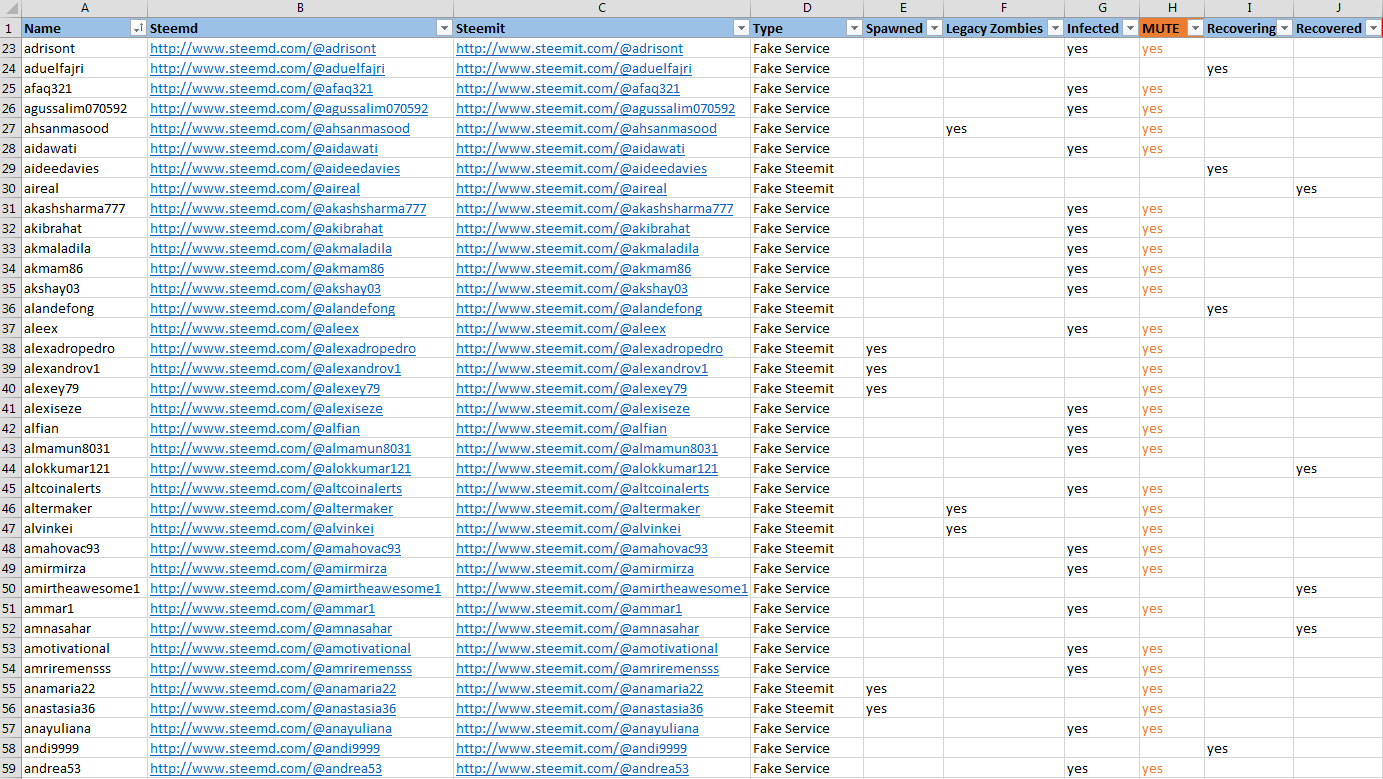 This is a screenshot of the Excel list.
This is a screenshot of the Excel list.
List Updates
Are you on the list in error?
If you recovered your account but we didn't catch it, let us know in the comments below or on the Steemcleaners Discord.
Do you know of an account that should be on the list?
Same as above.

Anti-Phishing Guides
Several guides were added to the repository to provide helpful information. Below are two of the newest guides. Additional guides can be found at the Repository.
Vectors
This is how most users become victimized.
Phishing Links
Many users click on phishing links that lead to look-alike websites that trick them to input their master password.
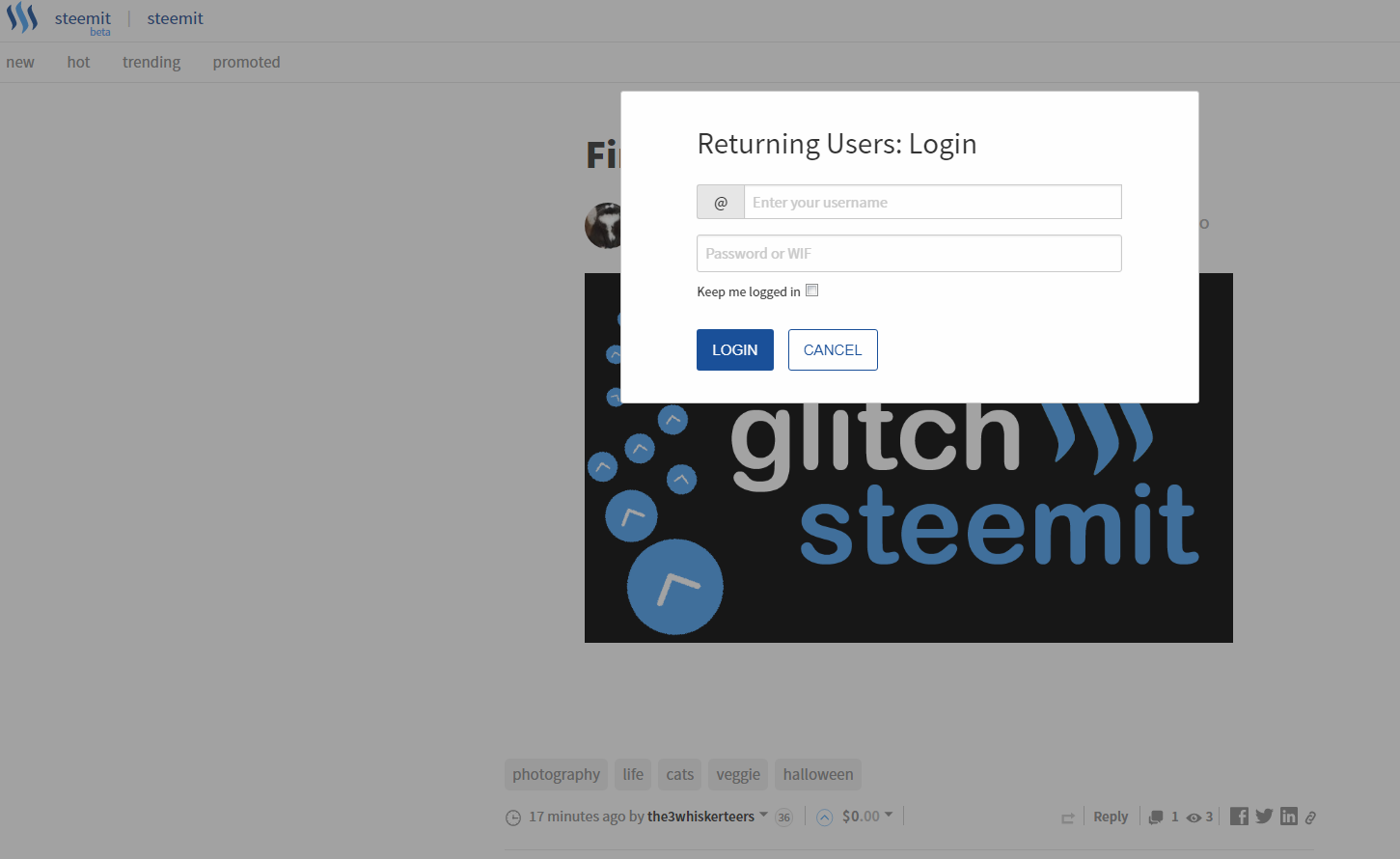 This is a screenshot of one of the fake websites the hackers made earlier on.
This is a screenshot of one of the fake websites the hackers made earlier on.
Accidental Key Reveal
The second most common way to lose control over one's account is by accidentally copy/pasting the master password in a memo or in a post. Hackers run "scrapers" that stream the blockchain looking for these accidental reveals.
Social Engineering
In several cases, hackers targetted specific individuals, tricking them in chat into clicking on phishing links or otherwise revealing their master password or keys.
Hacking
At least one user had their home computer compromised in search of their master password. The best way to remedy this sort of attack is to keep your master password in an encrypted container and backed up offline.
Mobile Malware
There are numerous cases of users downloading mobile apps from varous appstores that may look legitimate but are actually phishing.

Account Recovery
Accounts can be "recovered" after a password change within 30 days of the change. After 30 days have passed, the new password becomes permanent and irreveribly applied to the account.
Checking Recovery Account
The "recovery account" or "trustee account" is the account that has been set in the Steem blockchain to act as an administrator of your account. Typically, it is the account that was used to create your account. All accounts must be created by other accounts.

If you signed up through the Steemit.com website, your recovery account is @steem. You can check your recovery account by going to https://steemd.com/@yourusernamehere and searching for "Recovery account" on the left-hand side.
Accounts Created via Steemit.com
- Go to https://steemit.com/recover_account_step_1
- Put in the account name and your most recent recorded password.
- When prompted for an email address, be sure to use the email you used to sign up with.
- Monitor your email and wait up to 24 hours for your recovery email.
- If you don't get your email within 24 hours, go to steem.chat and ask for assistance in the #help room.
Accounts Created via 3rd Party Services
Each account creation service has its own recovery request form and is solely responsible for recovering the account. Steemit Inc has no way of conducting password recoveries of accounts made through 3rd party services.
AnonSteem
https://anon.steem.network 1. Go to https://anon.steem.network/recovery.html 2. Follow the directions on the website. You will need to provide a piece of verification as per Category 1 or 2 as outlined on the website. 3. Send an email with your information and verification to anonsteem [at] someguy123 [dot] com.
BlockTrades
https://blocktrades.us 1. Email support [at] blocktrades [dot] us. 2. Follow their instructions.
SteemCreate
https://www.steemcreate.com 1. Contact netuoso#9548 on Discord. 2. Follow his instructions.
SteemFounders
https://steemfounders.com 1. Contact the SteemFounders team on Discord here https://discord.gg/B6MgyRc. 2. Follow their instructions.
GuiltyParties
https://guiltyparties.com 1. Email guiltyparties [at] protonmail [dot] com to initiate your account recovery process. 2. Use the email you signed up with. Additional verification/details will be requested via email.
Sponsored via SteemConnect
- Determine who the trustee account is.
- Contact the trustee and ask them to recover the account.
- Direct them to the SteemDevs Discord here https://discord.gg/qTsSu9r should they require technical assistance.
Timelines
- 30 days is the time limit within which an account may be recovered.
- Passwords become permanent after 30 days.
- Trustee accounts become permanent after 30 days.
- Only one account recovery may be performed within a 30 days span.
- A password can only be changed once an hour.

Recovery Issues
There are three main things that hackers do to keep control of the Steem wallets and their funds.
Trustee Account Changed
If your trustee account has been changed, the password recovery procedure can still be initiated through your old trustee account. Trustee account changes take 30 days to become permanent. Watch for trustee account changes in Steemd and ask for help immediately after spotting them.
Active Authority Changed
You may still have control of your account but your active key has been compromised and altered. One tool to revoke the active authority is https://thenoblebot.herokuapp.com.
Vesting Route Changed
 A changed vesting route above is routing a victim's power down straight into the hacker's account.
A changed vesting route above is routing a victim's power down straight into the hacker's account.
The vesting route controls what account your account powers down into. Hackers often set it to their own accounts while they have control of their victims' accounts. The vesting route may be revoked to default using eSteem and Vessel.

Resource Links
Website: https://www.pofpofpof.com GitHub Repo - Hacked List: https://github.com/gryter/plentyofphish/blob/master/phishing.txt GitHub Repo - Guides: https://github.com/gryter/plentyofphish/tree/master/guides Steemcleaners Discord: https://discord.gg/kZ56egV