Many of you already know what I do on the side. I spend a good amount of my free time doing security analysis and penetration testing on web applications here in our Hive ecosystem. I do this voluntarily, without contracts or a fixed payment, which can sometimes lead to misunderstandings. But that is just how it is.

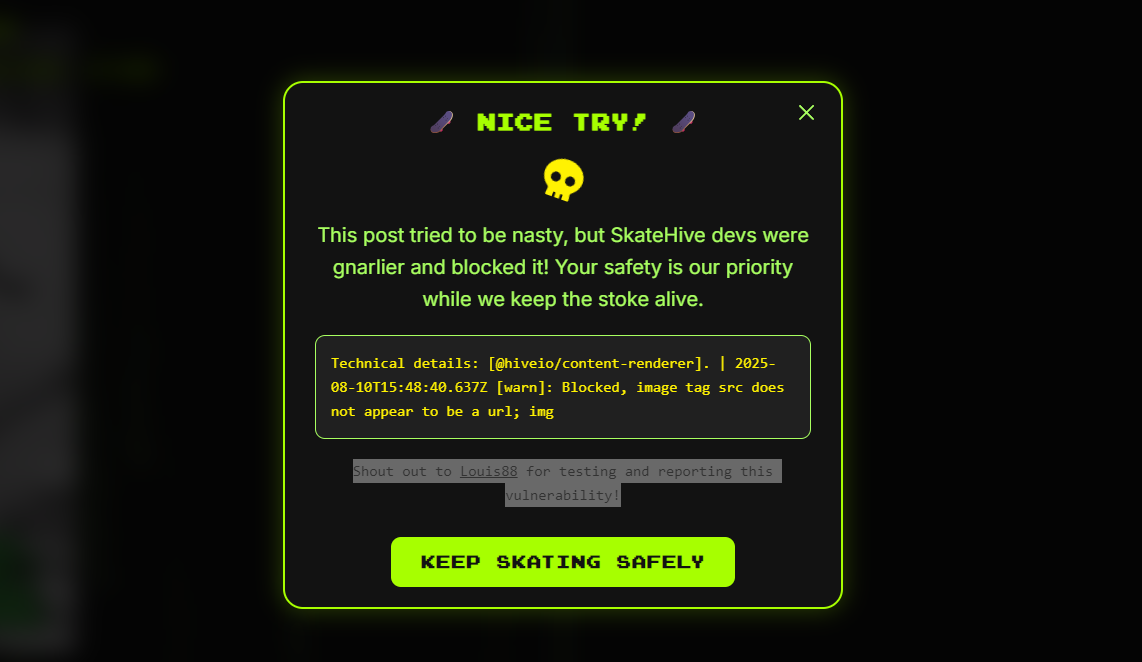
This morning, while enjoying my first coffee and scrolling through the Snaps on PeakD, I saw something new. A fresh frontend for skaters on Hive had just been released. Of course, I could not resist and jumped right into checking it for possible security issues. Unfortunately, I did not have to search for long before I came across vulnerabilities. It is something I have seen far too often in Hive projects.
I documented the details of what I found and sent everything directly to the Skatehive team. To their credit, they reacted quickly. They understood the situation immediately and began working on fixing the problems. After their first reply confirming the fix, I checked again and could not find any remaining issues. That is exactly how it should be. When there are security flaws in a public-facing frontend, sometimes every minute counts. A big thank you to the Skatehive team and especially to @xvlad for working so quickly and efficiently to close those issues.
Sadly, it is not always like this. In the past, I have often run into frontend developers who had no idea what I had just found. Many were not even aware of the risks these vulnerabilities carried. What makes it even harder is that I am using my own time, knowledge, and years of experience to help – and yet sometimes I do not even get a thank you. In a few cases, I have even been threatened or completely dismissed. That is frustrating, but as someone wearing the white or grey hat, I have to accept it.
It is a shame we do not have a bug bounty program on Hive. When you find security problems in a project that is doing very well financially, it feels strange not to have any formal recognition. I will not name the project yet, but I can say that there are still several very critical vulnerabilities in that frontend. At least one has a CVSS score of 8.1 (High) and could cause serious trouble if exploited. (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:N)
No matter how much some people might laugh at or dismiss my work as a security researcher, at the end of the day we are all using a platform that deals with real money. For some, it is not a small amount either. This is why I will not stop doing what I do.
So that was my Sunday. Sitting at my PC with perfect sunshine outside, plenty of coffee, and now finally an evening beer. A day dedicated to keeping Hive a little safer.
Thanks for reading and see you next time.
This show's up, when you try to do bad stuff now ;) GG