Hey everyone,
After my recent post about the follower cleanup script, @holoz0r mentioned that it would be neat to aggregate the account authorities of the people you follow/following to see who has given authority to other accounts. I thought that was a fantastic idea, and I couldn't resist writing a script to do exactly that.
The result is a new tool that scans your social graph (followers and following) and builds a local database of all the posting and active authorities granted between those accounts. It helps you map out the "web of trust" in your corner of the Hive ecosystem.
How it Works: Scan and Report
The script operates in two modes. First, you scan to collect the data, and then you report on what you've found.
1. Scanning Your Social Graph
When you first run the script with the scan command, it fetches your follower and following lists. It then iterates through each unique account to record who they have granted authority to, saving it all locally in an SQLite database file (authy.db).
After the scan is complete, it gives you a summary of the data it collected.
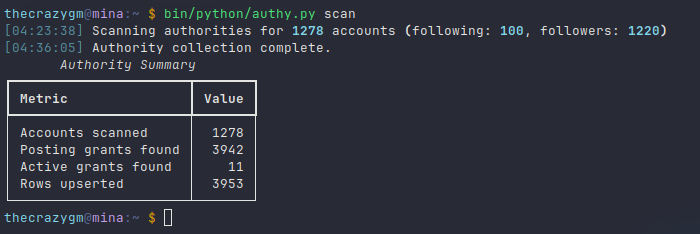
2. Reporting on the "Web of Trust"
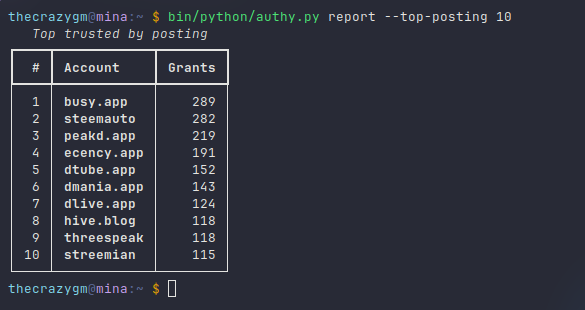
Once the scan is complete, you can run various reports to analyze the data. You can see who is most trusted with posting authority among the accounts in your social graph:
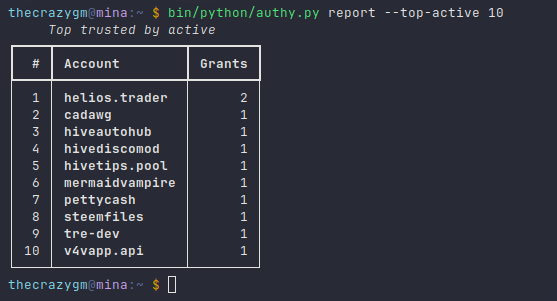
And you can do the same for active authority:
You can also drill down to see who a specific user, like @ecoinstant, grants authority to :
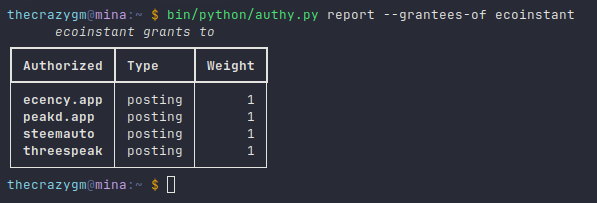
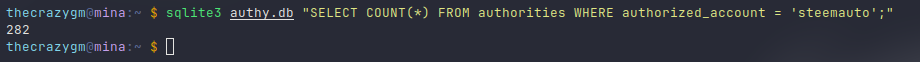
You can also run one to see who has granted authority to a user. (I would show you the result of:
bin/python/authy.py report --grants-to steemauto but let's just say it would be longer than this post.)
Get the Script
This tool offers a fascinating glimpse into the social trust layer of Hive. You can find the script in the Gist below. As I've mentioned before, you can run it directly from the URL using uv.
- GitHub Gist: https://gist.github.com/TheCrazyGM/1aaed40ca7d45104d982cc4fe77786b6
- Example Command:
uv run https://gist.github.com/TheCrazyGM/1aaed40ca7d45104d982cc4fe77786b6
Just make sure to set your POSTING_WIF environment variable before running it, it gathers the account information from that.
As always, Michael Garcia a.k.a. TheCrazyGM